[Analysis] Combatting ‘Procurement Fraud’ – Classification | Key Risks | Mitigation Strategies
- Other Laws|Blog|
- 4 Min Read
- By Taxmann
- |
- Last Updated on 17 September, 2024

Procurement fraud refers to illegal conduct that results in a financial or other advantage during the procurement process of goods, services, or contracts. It can occur at any stage of the procurement cycle, from the initial needs assessment and vendor selection to the final payment and contract closure. Organizations mitigate procurement fraud by implementing strict procurement policies, conducting regular audits, and promoting a transparent and competitive bidding environment.
By CA. Shrenik Shah – Partner | SN & Co.
Table of Contents
- What is Fraud?
- Classification of Fraud
- Procurement Fraud Statistics
- Atypical Forensic Approach
- Procurement Fraud Cycle
- P2P – Associated Risks
- Mitigation Strategies
- Frequently Asked Questions
- Prospects & Directories
1. What is Fraud?
1.1 Universal
Financial
Reward
Acquired
Under
Deception
1.2 Our Belief
Fair
Recovery
Acquired
Under Unfair
Doctrine
MATHS ON FRAUD = MQ < (O + P) R
MQ – Moral Quotient = (W * IQ)
O – OPPORTUNITY,
P – Pressure,
R – Rationalisation
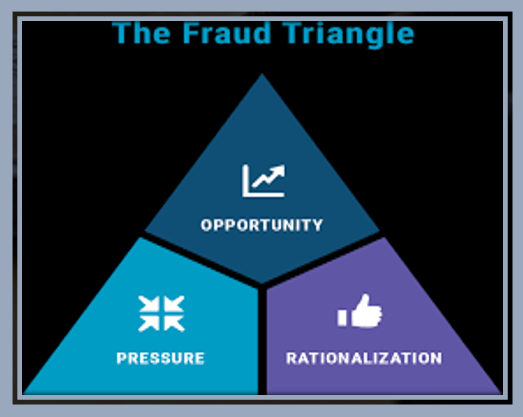
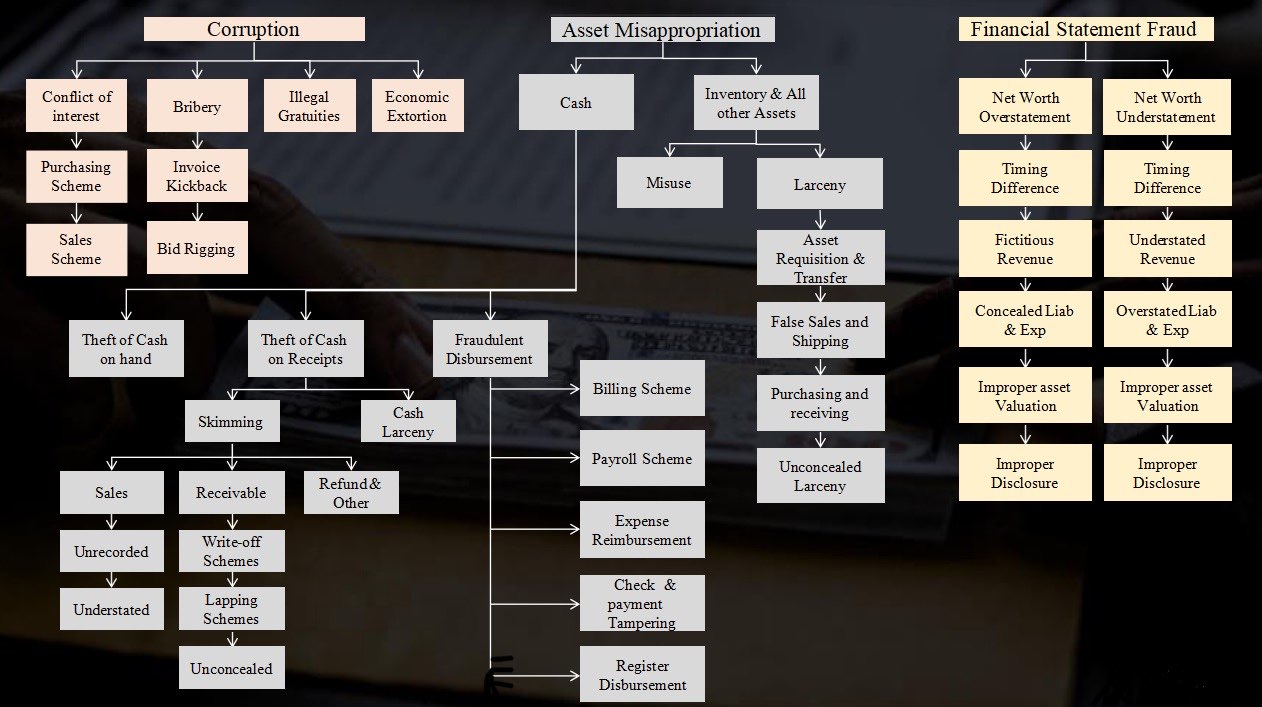
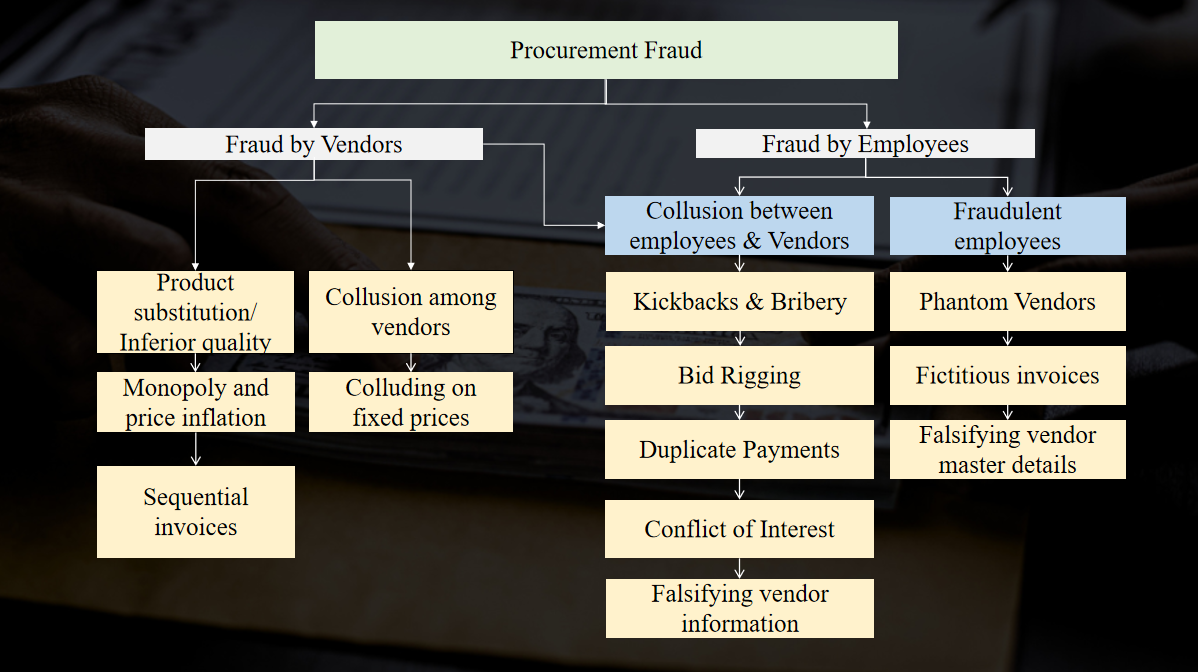
2. Classification of Fraud
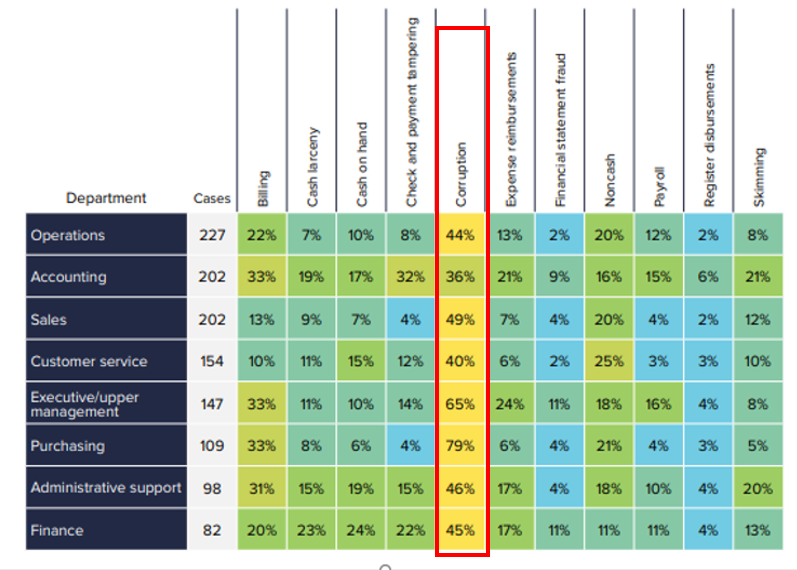
3. Procurement Fraud Statistics
Total Department wise Fraud Analysis (ACFE)
PWC – Global Economics Survey 2024 – 2500 companies
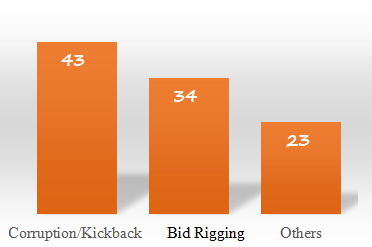
Highest Procurement Fraud Types
4. Atypical Forensic Approach
4.1 Atypical Approach– 7 Eye Theory
(1) Evidence Eye
- Without Evidence entire exercise is futile
- Need to be proven in court of law
(2) Theory Eye
- Gun Powder Theory
- Time Bomb Theory
- Inverse Logic Theory
- RSF Theory
- Benford’s Law Theory
(3) Tool Eye
- Tools play an important role while using investigative techniques
- GST, Logistics Tracking Tool, Background Verification Tool etc.
(4) Network Eye
- Market Intelligence
- Surveillance & Covert Operations
(5) Digital Eye
- Digital Forensic is scanning of emails, hard disk, mobile phones and recovery of deleted files , password cracker & so on
(6) Data Eye
- Data analytics – To identify duplications, irregularities, trends & patterns, link analysis, joining files, fund trail etc
(7) Your Eye
- Skeptical Attitude
- Connecting Dots Perspective
- Investigative approach
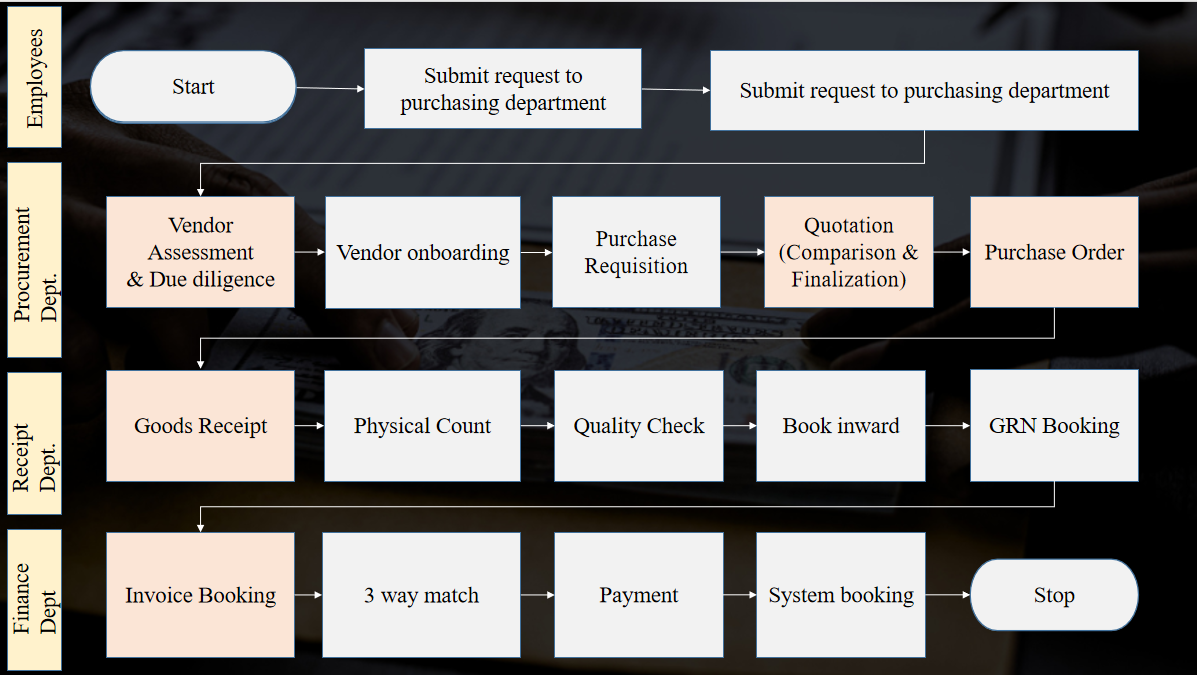
5. Procurement Fraud Cycle
Highlighted in red are areas having high susceptibility to fraud

6. P2P – Associated Risks
- No/Faulty due diligence conducted
- Feeble vendor assessment – Existing vendors
- Non-adherence to DOA/SOP
- Non-adherence to tolerance limit
- On account payments
- Regularization of backdated PO creation
- Substantial Credit Notes
- No blacklisting of inactive vendors
- QC clearance on defective goods/Non-existence of QC process
- Open PO for substantially higher period
- Vendor Favoritism – collusion with employe
- Lack of industry healthcheckRate Variance
- Inadequate quotations obtained
- Quotation comparison manipulations
- PO approved without PR and quotation – Order in excess of needs
- Vendor Creation prior to PO/GRN
- Inflation of Procurement Budget
7. Mitigation Strategies
7.1 Preventive
- Stringent Vendor Due Diligence Process
- Enabling quotation health check process
- Frequent Vendor Assessments
- Segregation of Duties & RPA (Robotic Process Automation)
7.2 Detective
- Internal Audit
- Surprise Vendor Surveillances
- Pretext Operations – Rate Variance
- Implementing Whistle blower mechanisms
7.3 Corrective
- Training & Awareness
- Revisiting Risk Appetite at company level
- Data analytics to find potential exceptions of perpetrator of fraud case & keep them under watch list
- Implementing ABAC policy & Taking action against violators
9. Frequently Asked Questions
- What are some recent procurement fraud cases/What are some red flags?
- What are the tools available in market for streamlining procurement process?
- What are some other departments who can have connivance with purchase departments?
- What are some inherent risks that would not be mitigated even after deploying proper procedures?
- Why is purchase such a vulnerable area for fraud?
10. Prospects & Directories
10.1 Our Directory
- Maths on fraud
- 7 Eye’s on fraud detection
- CVC technique for fraud prevention
- In-house Tools like Mail Scanning, SCAN, Mind Muneem
- Whistle-blow mechanism – Whistle-Eye
10.2 Takeaway
- Identification of procurement red flags
- Practical Knowledge
- Eye for detail readiness
- Procurement Tools & Software Knowledge
- Leveraging social media for fraud identification
10.3 Theory Directory
- Men to men marking theory.
- Cluster Theory
- Un-orthodox Theory.
- Connect the dot theory
- Confirmation Bias Theory
- Time Bomb Theory
- Corporate Espionage
- Hydro Theory
- Orphan Fund Theory
10.4 Current trends Directory
- ABAC- Revolutionary Regulation
- MCA stringent action on removal of shell companies
- Introduction of Forensic Standards
- AI and Data mining in forensic
Disclaimer: The content/information published on the website is only for general information of the user and shall not be construed as legal advice. While the Taxmann has exercised reasonable efforts to ensure the veracity of information/content published, Taxmann shall be under no liability in any manner whatsoever for incorrect information, if any.

Taxmann Publications has a dedicated in-house Research & Editorial Team. This team consists of a team of Chartered Accountants, Company Secretaries, and Lawyers. This team works under the guidance and supervision of editor-in-chief Mr Rakesh Bhargava.
The Research and Editorial Team is responsible for developing reliable and accurate content for the readers. The team follows the six-sigma approach to achieve the benchmark of zero error in its publications and research platforms. The team ensures that the following publication guidelines are thoroughly followed while developing the content:
- The statutory material is obtained only from the authorized and reliable sources
- All the latest developments in the judicial and legislative fields are covered
- Prepare the analytical write-ups on current, controversial, and important issues to help the readers to understand the concept and its implications
- Every content published by Taxmann is complete, accurate and lucid
- All evidence-based statements are supported with proper reference to Section, Circular No., Notification No. or citations
- The golden rules of grammar, style and consistency are thoroughly followed
- Font and size that’s easy to read and remain consistent across all imprint and digital publications are applied




 CA | CS | CMA
CA | CS | CMA
