E-Commerce Security and Controls – Introduction | Need | Security Threats
- Other Laws|Blog|
- 14 Min Read
- By Taxmann
- |
- Last Updated on 2 March, 2024

Table of Contents
- Introduction
- Dimension of E-commerce Security
- Security Threats In E-Commerce Environment
- Need of E-Commerce Security
- Security Controls
- Encryption
Checkout Taxmann's e-Commerce which offers a clear, systematic explanation of E-commerce concepts, enhanced with illustrations, real-world examples, chapter summaries, and review questions. It covers key topics such as the basics of e-commerce, technological foundations, security measures, web design, electronic payment systems, online business transactions, and e-retailing.
1. Introduction
E-Commerce companies face peculiar threats to security, by virtue of being connected on the internet. Internet was meant to be used for military and academic purpose. It wasn’t meant to be open for all, when it was conceived, initially. But that is history, Internet has since being used to conduct business transactions online. The whole ambit of things, including data (business and customer data), business policies, integrity of the transactions, etc need to be secured in order for the e-commerce functioning being smooth.
A cyber intruder doesn’t need to be physically present in the premises to cause disruption, he can remotely do it from a nearby building, city, country, rather from anywhere in the world. It may be days before the company gets to know that its system is being remotely manipulated.
In simple words
“E-commerce security threat refers to anything that has the potential to cause serious harm to a computer system and hence the whole set-up”
The intent in case of security breach is mala fide and may lead to loss in revenue to the business, whose security is threatened. The purpose of this article is to analyse the need and dimensions of security, analyze the threats surrounding it and provide solution for the same in terms of either encryption or laws in place.
2. Dimension of E-commerce Security
As discussed by Greenstein and Feinman in their book, “E-Commerce- Security, Risk Management and control”, they’ve laid down four security concerns, which create the need for a stringent security system in place.
- Data integrity: There is just too much data involved in any business EDI i.e. electronic data interchange has facilitated e-commerce transactions but at the same time, the data is vulnerable and can be stolen and misused to the disadvantage of the company. The company’s own internal data needs to be protected and at the same time, the website data needs security since that is the face of the business.
- BusinessPolicies: The policies of the business are for internal use and some are for the references of the Business Partners (intranet and extranet). These policies, like bill payment and billing policies, shipping policies, return policies, etc. need to remain intact since if changed by unauthorized, person it would lead to chaos.
- Integrity of Transaction Processing: It is imperative that the transaction must happen the way, they are agreed upon. The system should be impeccable, so that the customers’ orders are taken well, processed and delivered on time. The compromise in the transaction processing may lead to misplaced orders to wrong orders being delivered.
- Privacy of data: Privacy policy should be stated and followed so that the customer or the visitor’s data is not used against their will. The stolen data of the customers or the visitors can lead to huge losses.
- Uninterrupted availability: A secured e-commerce system shall be able to provide uninterrupted availability to the customers, business partners and employees.
- Non-repudiation: E-commerce security makes sure that either of the party cannot deny the deals entered to, online.
3. Security Threats In E-Commerce Environment
Security threats in e-commerce have varied implications depending on the intentions of person or the organisation breaching the security. The following figure shows the various implications of Security breach.
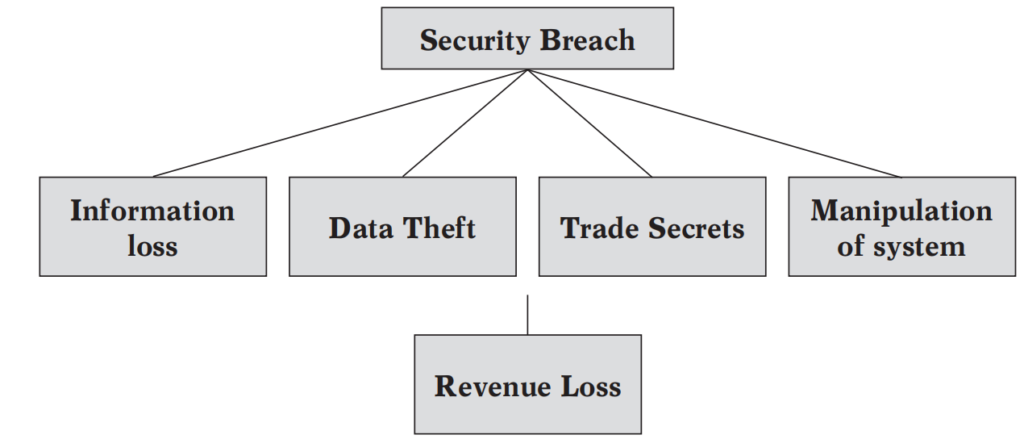
Some implications of Security Breach
The security breach is of various types like phishing, trojan horse, cyber squatting, etc (discussed below), but the reasons for the same are enlisted below:
- Information loss: The security breach may be for the reason of causing harm to the business by deleting important information from the business.
- Data Theft: Stealing of customer data to target them one on one, may be one of the reasons.
- Trade Secrets: The intention of the breacher, may be to steal the trade secret and use it for his own benefit.
- Manipulation of the system: The system may be manipulated in such a way, that it keeps sending unsolicited and unplanned information to the users, or may not allow the site to function properly.
3.1 Threats in E-Commerce
The threats in E-commerce are aplenty and can be categorised into the following categories:
- Client Threat
- Communication Channel Threat
- Server Threat
- Miscellaneous Threats
3.1.1 Client Threat
Client threats are a result of dynamic webpages. Thhen the webpages were static, the threats were less. But e-commerce is possible only due to the dynamism of the webpages, whether it is comparing prices or adding things to cart or making the payment. The following threats fall in the category of Client threats:
a. Trojan Horse: A simple looking, harmless file may be downloaded, which would release innumerable viruses into the system. The virus may appear to be a harmless data file or an executable file, which once run may cause data theft or other harm to the system, where released. The malicious instructions in the Trojan horse threat remain hidden, but are being executed causing harm to the client system.
b. Cookies: Cookies are amongst the biggest threat to the customer privacy. Cookies are small programs which are installed on the customer’s browser and record there browsing activities which include the logins, passwords, buying or viewing patterns. The companies rely on cookies to study the customers and target them accordingly but at the same time, each movement of the customer online is tracked and can be traced. Any malicious intent of using the cookies for ulterior motives can lead to huge losses for the customers.
c. Virus: Threats from virus are real and affect the client system ad- versely. A computer Virus is a programme or a code that is loaded onto a computer without the knowledge of the user and run against the command of the user. Certain programmes can be downloaded online to run a certain application e.g. Java Script, Active X control; which may be a danger to the privacy and integrity of the system since they might be corrupted to act in a malicious way.
3.1.2 Communication Channel Threat
Communication online links the consumer with the e-commerce partners. The message takes the form of packets from one point of connection to the other. The packets access different paths before getting sorted out and reaching the final destination. It is very difficult to guarantee that every computer on the Internet through which messages (packets) pass is safe, secure and non-hostile. In all likelihood, someone can reach the message rendering it incomprehensible or altering it to convey something else or completely eliminate the message. These threats are termed as Communication Channel Threats. The various threats under this category are:
a.Threats from Sniffer Programs: A sniffer program monitors the data flowing on the internet, in real time. All sniffer programs are not bad, some are legal as well. Sniffer programs can read e-mail messages as well as any e-commerce communication. This illegal deciphering of messages may lead to huge corporate losses, when confidential information is being shared.
b.Integrity threats: These threats are prevalent in the banking industry. The banking transaction information is not only deciphered but also altered online. For example, an amount of ` 5000 is being transferred online, the integrity threat implies that the amount may be changed to ` 50000, during the online payment process.
c. Cyber Vandalism: ‘Vandalism’ refers to the act involving damaging or destruction of public or private property. Cyber Vandalism refers to the act of altering, deleting or adding content to someone else’s digital content or website. More often, cyber vandalism is not executed for financial purpose but to prove the programming superiority or just for fun.
d. Spoofing: The creating of websites and getting a domain name, is the simplest of the things, related to e-commerce. Spoofing is the unethical art of sending communication from an unidentified source emulating the identity of another person. e.g. e-mail spoofing is easy to comprehend, an e-mail address to make people believe its a message from someone, it actually isn’t. e.g. getting a mail from a falsified account of a friend, asking to EFT some money, to them as they were in emergent need. And later getting a mail from a friend saying that they never sent any such mail.
e. Necessity Threats: The necessity threat is the one in which the system is slowed down to such an extent that it doesn’t let the system operate properly. Slowing down of the whole process, drives the customers away e.g. if the payment process is slow, it would lead to unrest with the customer.
3.1.3 Server Threat
Server is the connect between the Internet and the user. The server is vulnerable to threats, and if the security of the server is compromised, a lot of data can be misused.
a. Web server threat: The most profound information in todays times of e-Commerce and e-payments are the usernames and the passwords. The web server threat may be extremely detrimental if the security of this privilege is breached. All the confidential and integral information needs to be protected at the web server end. It is known that if the Webserver software is complex, the probability of errors is higher and it gives easy access to the people with bad intent.
b. Database Threats: The companies maintain a database of all the information including B2C information i.e. the product information, user information, orders and payment information, sales returns information, etc. E2E i.e. the communication amongst the employees of the company, etc. This database, if breached and shared unscrupulously would result in huge losses to the company in terms of customer data or confidential private data of the company.
c. CGI Threats: Common gateway interface as the name suggests is an interface between the web browser and the web server. The request from the web browser is routed to the server through CGI, which sends out the output as per the input received. CGI is crucial for smooth and correct flow of information and it is under perpetual threat from the attackers. Once CGI is compromised, the request from the browser may not reach the web server or the web server’s output may be misdirected to some other browser.
d. Website Masquerading: Masquerade is a disguise and the website which is disguised by unscrupulous users is a great threat. The unattended logged in websites can be hacked into and anyone can gain unauthorised access to the system. The unprotected system can become vulnerable to a masquerade attack from insider or an outsider. It all depends on the level of security and attentiveness on the part of the user.
The attacker can have easy access to the point of entry due to weak authentication process.
Once authorised for entry, the attacker would have full access to the data base and may deface the website, make it incomprehensible or changing the nature of the website or defaming the website by putting detrimental slogans, etc. It may be able to modify and delete software and data, and make changes to network configuration and routing information.
3.1.4 Miscellaneous Threat
a. Phishing: Phishing is a homophone of fishing. Just like fishing, the target is trapped or lured into sharing with fraudulent people. Phishing refers to the fraudulent practice of sending e-mails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.
The e-mail seems to be from a legitimate person, thereby making the task of hacker easier, since the user may share the details without hesitation.
The only purpose of phishing is to steal money. This is done by either making the user clicking on a link which installs a malicious software in the system. The other way is to seek personal information from the user.
Here is an example of what a phishing scam in an e-mail message might look like.
Hello!
As part of our security measures, we regularly screen activity in the Facebook
system. We recently contacted you after noticing an issue on your account.
Spelling -> Our system detected unusual Copyrights activity linked to your Facebook account, please follow the link bellow to fill the Copyright Law form:
Links in email -> http://www.facebook.com/application_form
Threats -> Note: If you don’t fill the application your account will be permanently blocked
Regards
Popular Company -> Facebook Copyrights Department
Example of Phishing
Source: https://www.microsoft.com/en-us/safety/online-privacy/phishing-symptoms. aspx
The ways to spot a phishing threat is bad spellings and grammar, sus- picious e-mail message, the link may also lead you to.exe files. These kinds of files are known to spread malicious software. Sometimes, the mail threatens to block either an e-mail account or social networking account. Sometimes, spoofing popular websites or companies to add credibility to the mail.
b. Hacking: Hacking is defined as gaining of unauthorised access into the system or computer. It is an act of intrusion, which by term it- self is unauthorised. The person who executes the task of hacking is termed as a “hacker”. Hacker are “clever programmers” who know how to get into a system without authorised access.
The reasons for hacking may be to access information, change data, cause damage, prevent authorised access, etc. According to the reason, a person decides to hack they are categorised differently Sometimes, the professionals have to check the strength of security of their own systems, when they hack the system they are called White hat professionals.
Hackers who undertake hacking for personal gains, to destroy steal or denying access they are termed as Black hat hackers. They can destroy, steal or even prevent authorised users from accessing the system. They do this by finding loopholes and weaknesses in the system. Some computer experts call them crackers instead of hackers. Grey hat hackers comprise curious people who have just about enough computer language skills to enable them to hack a system to locate potential loopholes in the network security system.*
*(http://economictimes.indiatimes.com/definition/hacking) –
c. Cyber Squatting: Cyber Squatting is the process of registering the same or similar domain name of a reputed firm, with the intent of reselling the same at exorbitant price. It is also to confuse people into buying from them, thinking its a known brand. Its also known as domain squatting. The word squatting refers to the practice of inhabiting someone else’s property without their permission.
Additional Reading
Cyber Squatting
Arun Jaitley, Finance Minister of India, is the well known politician and leader of the BJP. He wished to register the domain www.arunjaitley.com but found that the domain had already been registered as of the year 2009.
The motive is always ulterior, either to get people to buy from the same or misspelt name or to resell the domain name. The propaga- tion of many top level domain names (TLD) like.com,.org,.net,.in, etc. makes it easier to copy the names or misspell them.
d. Intellectual Property Threats: The ease with which data can simply be downloaded and stored without seeking the permission of
the Intellectual Property rights owner, has made it a big threat. e.g. Digital files, works, designs can be copied and disseminated, online or offline, with ease.
3.2 Why do web attackers breach E-Commerce Security?
The attackers may have different motivations to breach the security of the system. It may range from mala fide intentions of data theft or monetary theft or just to show their technical superiority.
The hacker may want to
- access confidential information about the company and/or its users data.
- corrupt the information on the website.
- modify the system to work according to the hackers intent.
- block access to the system at their discretion.
- just to prove their technical superiority, without any mala fide inten- tion.
4. Need of E-Commerce Security
The threats to security are a plenty and they involve high risk to the authenticity, integrity and privacy of the e-commerce companies. The detailed discussion on the need for E-commerce companies to invest in the security, is as follows:
a. Confidentiality: The information shared on the internet (between business and the customers, extranet (amongst business partners) and intranet (amongst the employees) is all confidential and any access by the outside forces with mala fide intent can cause huge losses for the company.
b. Virus Protection: The e-commerce systems are susceptible to many attacks, amongst those are the virus attacks which manipulate the system to act in a peculiar way and can spread on its way without further interference by the hacker. The reputation of an e-commerce company is harmed when the undesired actions are accomplished through the website e.g. repetitive e-mails which spam the system, etc.
c. Integrity: The website is the face of the company. The users know the store as they see it. If the attacker changes or deletes the content of the website; the users might be driven away from the e-commerce business.
d. Availability: It requires tremendous effort on the part of the e-commerce organisation to get the customer to their website, therefore it is important that the website is available all the time. Interrupted availability or slow working website, due to some security breach would be detrimental to the success of the company.
e. Non-repudiation: Online actions need a different level of security since there is no physical interaction amongst the parties. Online security ensures that neither of the parties can deny entering into the agreement and the terms remain the same.
f. Digital India: Launched in 2014, Digital India initiative aims to make the transactions between the Government and the citizens online and electronic. Digilocker is also a part of Digital India, can be referred to, in order to explain the need for Digital Security. DigiLockers are supposed to store all the important documents, electronically. Unless, fully secured, this facility poses a great threat.
g. Digital Convergence: Laptops, tablets, smart phones, some smart watches can be used for conducting e-commerce. The users keep themselves logged in to almost all the gadgets at all times, hence increasing the risk of threats and hence security. The security threats are across platforms and the needs are also across all of them.
h. Too big, too soon: The space has expanded too soon and for all the loopholes to be plugged, it requires more time and better technology.
i. Evolving attackers: The attackers are evolving with the evolving technologies. They need to be tackled by creating security control system that can out-smart them.
j. Internet penetration: The new segment of users are being added everyday. The unawareness of the security threats by the new users keeps the need for security.
5. Security Controls
The analysis of various threats and the need for security, takes us to this point where the discussion on Security Controls ensues. The starting point would be the Threats and from there the controls required. The network security, client security, data security, all have been discussed above, need to have security controls for the smooth running of e-commerce organisations. The security are discussed below:
(i) Password: The alphanumeric characters that serve as passwords are a powerful way of security control. Passwords are unique to a machine or a website. This is the most commonly used security control system. To remain effective and relevant, the password should be of considerable strength i.e. not too simple to guess; and should be changed frequently.
(ii) Virus Control: Virus attacks are quite prevalent and since they replicate themselves, the virus control is required at all points of access. Virus attacks have been explained in Section 3.2.1 (I)(c). The e-commerce companies make efforts to mange the virus which may enter the clients system while downloading a file from the company’s website. The antivirus are required to be used and updated regularly since newer viruses are being developed at a fast pace and in high numbers. Virus control is of paramount importance since the customers are very hard to get, they are not disillusioned due to virus infection.
(iii) Biometric System: Using some body part, as a measure to allow access to the users/client’s website or machine is another good security control method. Finger prints, palm prints, voice recognition, retinal patter, etc. can be used to allow only the authentic user to access the system. E.g. BHIM Aadhaar app launched in India on April 14, 2017, uses the biometric system of thumb impression to transfer funds from the bank account.
(iv) Firewall: Firewall is a system where the access is controlled between the two networks. To access the network protected by a firewall, the hacker has to penetrate the firewall with the help of user name and password. Hence the firewall keeps the unwanted access in check. Firewall is one of the most common ways to check the unauthorised entry into the system and is normally used during online payments. It is not easy to permeate a firewall since the firewall filters all messages coming in and going out. To enter a firewall, normally a user name and password combination is used. If the user name and passwords don’t match, the unwanted user and malicious codes are kept at bay.
Concern of a Businessman and a User
Online Business Man
What if my website is hacked? I am concerned about the:
- Employee information
- Tender information
- Marketing information
- Proprietary information, etc
Online Customer
I am concerned about the
- Fraud by hackers
- Privacy i.e. personal information
- Authenticity of the data, its integrity, etc
- Financial information, etc
6. Encryption
There was a time, when hard copy of all the documents, were either hand delivered or through the post but as discussed in the earlier section, the online content is exposed to a variety of threats, the technological solutions of the same.
Online environments’ success depends on the fact that the transactions that take place are secure whether it is financial transactions, personal information, etc.. The major hiccup in the initial take-off of web was the fact that customers, businesses and users, all were apprehensive that the transactions on the web were not secured and could be tempered with. All the parties were concerned about the information important to them.
For example:
To help resolving the concerns of the customers as well as the business, encryption evolved. Encryption is a process of disguising data in such a form that it can be understood or is legible only to the parties concerned. Implying that the message that is encoded can be decoded only with the help of a key. This technique dates back to the time immemorial when the transmission of confidential data was done by encrypting it. Any form of online transaction cannot be done without encryption. To simplify it, a business deal cannot be struck if both the parties, who are geographically apart, are not sure that the content is not meddled with during the transmission.
It is also referred to as a basis of network security.
6.1 Understanding Encryption
Encryption refers to the scrambled data (i.e. encoded data) which can be sorted (decoded) with the help of a key which is a series of electronic signals stored on the PC.
Encryption is a mathematical procedure that scrambles data so that it is extremely difficult for any one than the authorized recipient to recover the original message.
The translation of data into a secret code. Encryption is the most effective way to achieve data security. To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it. Unencrypted data is called plain text; encrypted data is referred to as cipher text.
Evidently, it involves two parties-one, which encodes the data and the other for whom it is meant for, i.e. the one who can decode it. Both the parties should be aware of the format followed.
6.2 Need of Encryption
Encryption is done so that there is no violation of PAIN i.e. privacy, authentication (verification/validation), integrity (veracity/reliability) and non-repudiation (non-denial, non-negation/non-refutation). In simple words, whenever data is transmitted over the net it is important to protect it from falling into wrong hands and being corrupted during transmission and all the essentials of the transaction namely privacy, validity, reliability and non-refutation, remain intact.
Disclaimer: The content/information published on the website is only for general information of the user and shall not be construed as legal advice. While the Taxmann has exercised reasonable efforts to ensure the veracity of information/content published, Taxmann shall be under no liability in any manner whatsoever for incorrect information, if any.

Taxmann Publications has a dedicated in-house Research & Editorial Team. This team consists of a team of Chartered Accountants, Company Secretaries, and Lawyers. This team works under the guidance and supervision of editor-in-chief Mr Rakesh Bhargava.
The Research and Editorial Team is responsible for developing reliable and accurate content for the readers. The team follows the six-sigma approach to achieve the benchmark of zero error in its publications and research platforms. The team ensures that the following publication guidelines are thoroughly followed while developing the content:
- The statutory material is obtained only from the authorized and reliable sources
- All the latest developments in the judicial and legislative fields are covered
- Prepare the analytical write-ups on current, controversial, and important issues to help the readers to understand the concept and its implications
- Every content published by Taxmann is complete, accurate and lucid
- All evidence-based statements are supported with proper reference to Section, Circular No., Notification No. or citations
- The golden rules of grammar, style and consistency are thoroughly followed
- Font and size that’s easy to read and remain consistent across all imprint and digital publications are applied



 CA | CS | CMA
CA | CS | CMA
